IKEv2
Internet Key Exchange version 2 (IKEv2) is a tunneling protocol, based on IPsec, that establishes a secure VPN communication between VPN devices and defines negotiation and authentication processes for IPsec security associations (SAs).
1 IKEV2 General
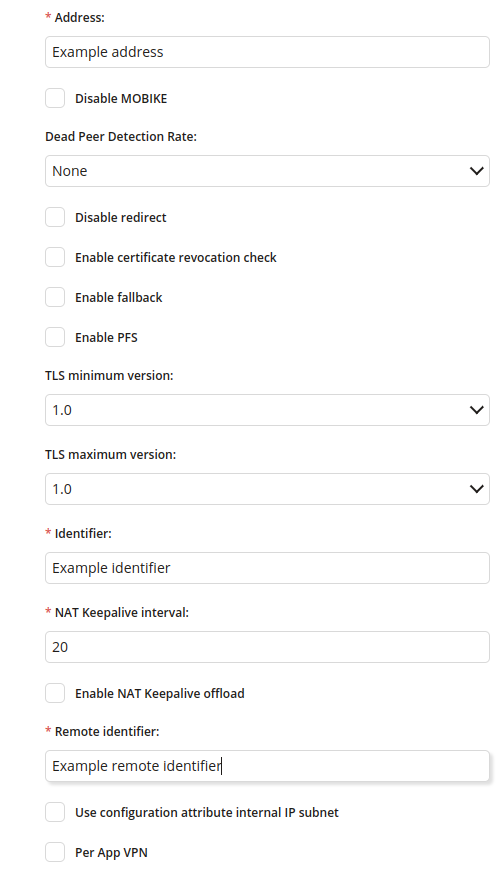
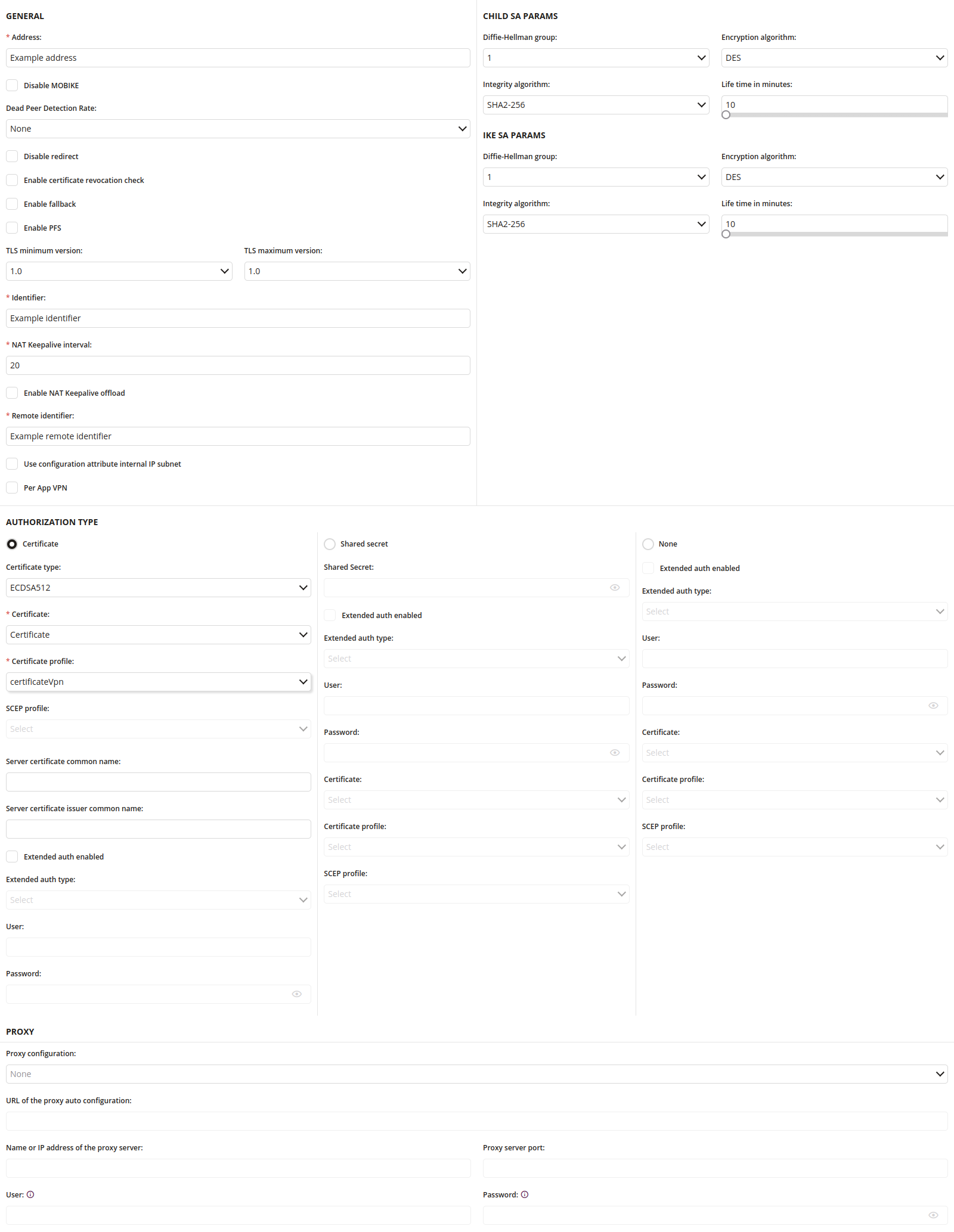
1.1 Address
- Enter the address URL
- Required
1.2 Disable MOBIKE
- If checked, MOBIKE is disabled
- MOBIKE allows to remain connected to the VPN even if user move to a different network
1.3 Dead Peer Detection Rate
- The frequency at which the IKEv2 client will run the dead peer detection algorithm
- One of:
- None
- Low (every 30 minutes)
- Medium (every 10 minutes)
- High (every 1 minute)
1.4 Disable redirect
- If checked, IKEv2 server redirects are disabled
1.5 Enable certificate revocation check
- If checked, evocation checking of the IKEv2 server certificate is enabled
- If checked, during IKEv2 negotiation the certificate identifying the server is checked to see if it has been revoked
1.6 Enable fallback
- If checked, enable the use of cellular data when Wi-Fi connectivity is poor
1.7 Enable PFS
- If checked, Perfect Forward Secrecy is enabled
1.8 TLS minimum version
- One of:
- 1.0
- 1.1
- 1.2
1.9 TLS maximum version
- One of:
- 1.0
- 1.1
- 1.2
1.10 Identifier
- Enter the local Identifier of the IKEv2 client
- Required
1.11 NAT Keepalive interval
- Enter the frequency in seconds at which gateway sends NAT Keepalive packets to its peer to keep the NAT session alive, so that the peer can access the device
- Minimum value is 20
- Maximum value is 1400
- Required
1.12 Enable NAT Keepalive offload
- If checked, Keepalive packets will be offloaded to hardware while the device is asleep
1.13 Remote identifier
- Enter the Remote Identifier of the IKEv2 client
- Required
1.14 User configuration attribute internal IP subnet
- If checked, split tunnel configurations won’t be communicated via traffic selectors during IKE negotiation
1.15 Per App VPN
- If checked, allows to use VPN configuration per application
2 Child SA Params
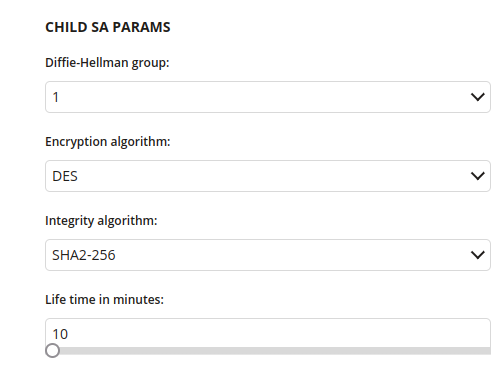
2.1 Diffie-Hellman group
- Diffie-Hellman groups determine the strength of the key used in the key exchange process
- One of:
- 1
- 2
- 5
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 31
2.2 Encryption algorithm
- Type of encryption algorithm. Defines how strong security will be.
- One of:
- DES
- 3DES
- 3DAES-128ES
- AES-256
- AES-128-GCM
- AES-256-GCM
- ChaCha20Poly1305
2.3 Integrity algorithm
- Type of integrity algorithm. Defines how strong security will be.
- One of:
- SHA1-96
- SHA1-160
- SHA2-256
- SHA2-384
- SHA2-512
2.4 Life time in minutes
- The duration of the lifetime of the Security Association
- Minimum value is 10
- Maximum value is 1440
3 IKE SA Params
3.1 Diffie-Hellman group
- Diffie-Hellman groups determine the strength of the key used in the key exchange process
- One of:
- 1
- 2
- 5
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 31
3.2 Encryption algorithm
- Type of encryption algorithm. Defines how strong security will be.
- One of:
- DES
- 3DES
- 3DES-128ES
- AES-256
- AES-128-GCM
- AES-256-GCM
- ChaCha20Poly1305
3.3 Integrity algorithm
- Type of integrity algorithm. Defines how strong security will be.
- One of:
- SHA1-96
- SHA1-160
- SHA2-256
- SHA2-384
- SHA2-512
3.4 Life time in minutes
- The duration of the lifetime of the Security Association
- Minimum value is 10
- Maximum value is 1440
4 Authorization Type – Certificate
4.1 Certificate type
- One of:
- RSA
- ECDSA256
- ECDSA384
- ECDSA512
- Ed25519
4.2 Certificate
- Type of certificate that is created in Proget system
- One of:
- Certificate
- SCEP
4.3 Certificate profile
- Name of Certificate profile which will be used
- Required if ‘Certificate: Certificate’ is chosen
4.4 SCEP profile
- Name of SCEP profile which will be used
- Required if ‘Certificate: SCEP’ is chosen
4.5 Server certificate common name
- Enter a string containing the value of the Subject Common Name field of the IKEv2 server’s certificate
4.6 Server certificate issuer common name
- Enter a string containing the value of the Subject Common Name field of the Certificate Authority certificate that issued the IKEv2 server”s certificate.
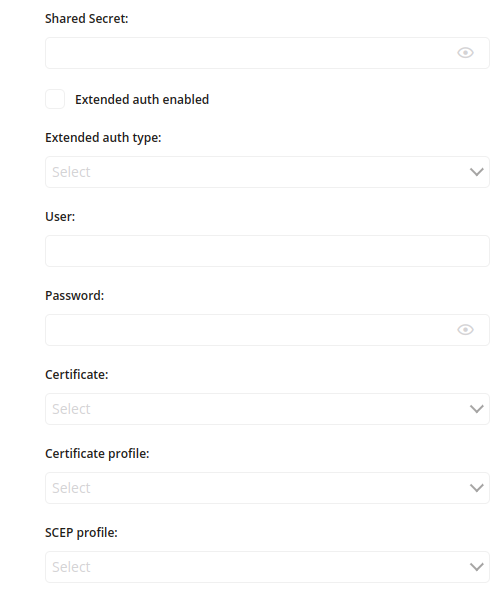
4.7 Extended auth enabled
- If checked, allows to use extended authorization
4.8 Extended auth type
- One of:
- User
- Certificate
- Required if ‘Extended auth enabled’ is checked
4.9 User
- Enter the name of the user
- Required if ‘Extended auth type: User’ is chosen
4.10 Password
- Enter the user password
- Available if ‘Extended auth type: User’ is chosen
5 Authorization Type – Shared secret
6 Authorization Type – None
6.1 Extended auth enabled
- If checked, allows to use extended authorization
6.2 Extended auth type
- One of:
- User
- Certificate
- Required if ‘Extended auth enabled’ is checked
6.3 User
- Enter the name of the user
- Required if ‘Extended auth type: User’ is chosen
6.4 Password
- Enter the user password
- Available if, ‘Extended auth type: User’ is chosen
6.5 Certificate
- One of:
- Certificate
- SCEP
- Required if ‘Extended auth type: Certificate’ is chosen
6.6 Certificate profile
- Chose the name of Certificate profile which will be used
- Required if ‘Certificate: Certificate’ is chosen
6.7 SCEP profile
- Chose the name of SCEP profile which will be used
- Required if ‘Certificate: SCEP’ is chosen
7 IKEV2 Proxy
7.1 Proxy configuration
- One of:
- Automatic
- Manual
- Proxy servers act as relays between the website you’re visiting and your device
7.2 URL of the proxy auto configuration
- Enter the URL thought which all browser traffic will be rerouted
- Required if ‘Proxy configuration: Automatic’ is chosen
7.3 Name or IP address of the proxy auto configuration
- Enter the IP address or host name of the VPN server
- Required if ‘Proxy configuration: Manual’ is chosen
7.4 Proxy server port
- Enter the port number which is a part of the addressing information used to identify the receivers and senders of network messages
- Minimum value is 0
- Maximum value is 65535
- Available if ‘Proxy configuration: Manual’ is chosen
7.5 User
- Enter the name of user account for proxy authentication
- Available if ‘Proxy configuration: Manual’ is chosen
7.6 Password
- Enter the password of user Proxy authorization
- Available if ‘Proxy configuration: Manual’ is chosen