MTP
MTP profile monitors the device and detects potential threats to which it may be exposed. In addition, the profile allows you to configure specific responses to the security incident detected.
Compatibility:
- Android
- Android Enterprise Device Owner
- Android Enterprise Profile Owner
1 Name
- Enter the name of the MTP profile
- Maximum length of the text is 255
- Required
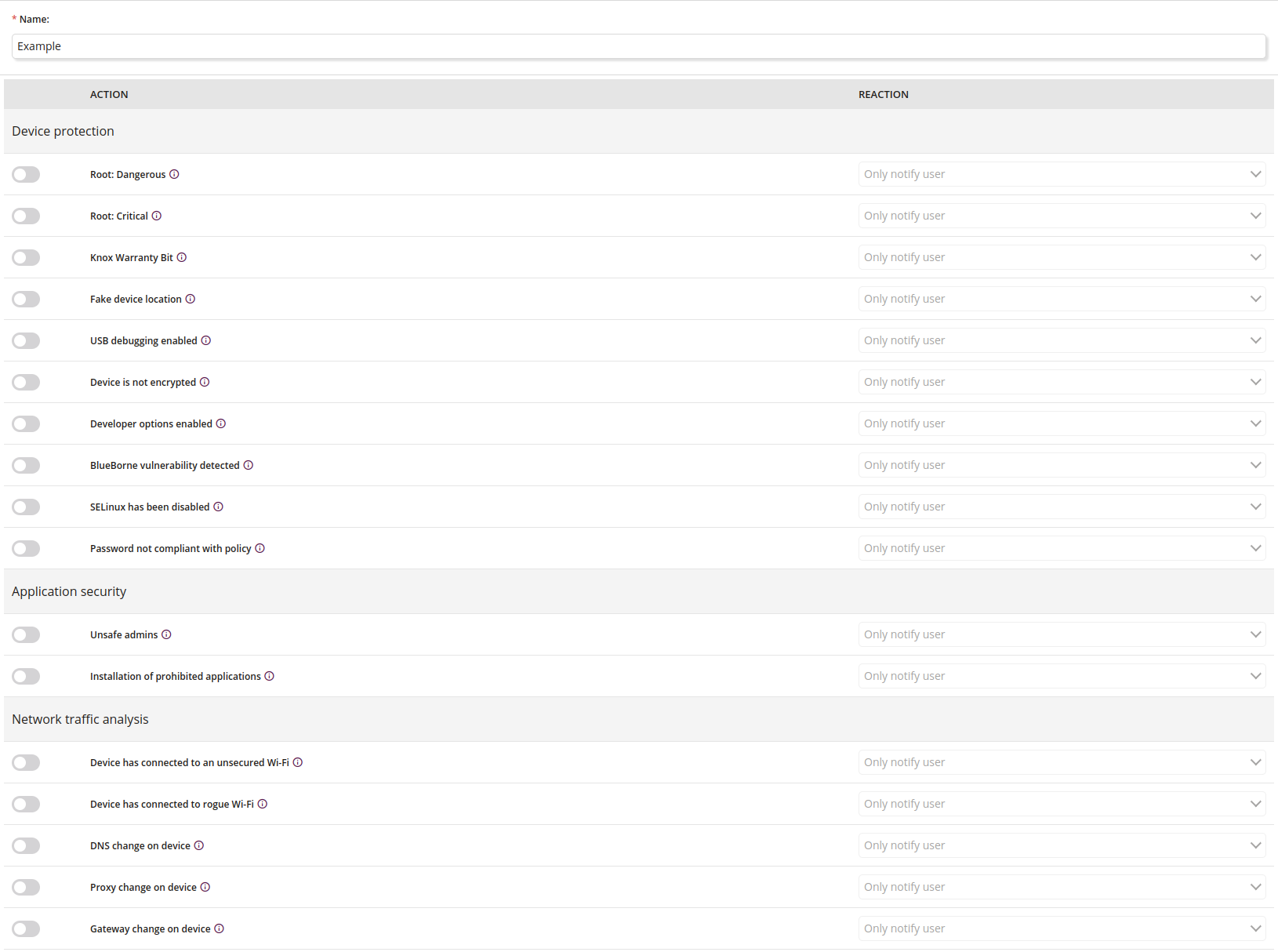
2 Device protection
2.1 Root: Dangerous
- Files used to root have been detected on device. However, this does not mean that device has been rooted. There are known cases when device was pre-loaded with such files in memory.
2.2 Root: Critical
- Rooting is process of obtaining unauthorized access or elevated permissions on the system. It can potentially create security loopholes that may not be easy to find or bypass device security measures.
2.3 Knox Warranty Bit
- The Samsung Knox warranty bit is a security feature that detects if unofficial software has been installed on device. This helps prevent malicious attempts from accessing data. The Knox Warranty Bit detects if a non-Knox kernel has been loaded on the device. It is a one-time programmable bit e-fuse. If a non-Knox boot loader or kernel has been installed on the device, Knox can no longer guarantee the security.
2.4 Fake device location
- The device presents a fake location. The use of a false location can be used to confuse device monitoring systems, including systems granting access to corporate resources based on the location of the device (e.g. geofencing). Feature unavailable on Android Enterprise Profile Owner. The feature requires the use of a location profile to work properly.
2.5 USB debugging enabled
- USB debugging is a configuration option for development purposes only. By enabling USB debugging, device can accept commands from a computer via a USB cable. Does not work for Android Enterprise Profile Owner.
2.6 Device is not encrypted
- When device is not encrypted, the data contained on it is not secured
2.7 Developer options enabled
- Developer options are configuration options intended for development purposes only. Once enabled, user can change advanced settings which threatens the integrity of the settings and the security of the device. Does not work for Android Enterprise Profile Owner.
2.8 BlueBorne vulnerability detected
- BlueBorne is an attack that uses a Bluetooth connection to penetrate and take control over device. To avoid any risk associated with BlueBorne, it is recommended that user permanently turn off Bluetooth until device manufacturer or mobile network operator updates operating system. If the use of Bluetooth is necessary, it is recommended to run only in a safe area and only for the time of its use.
2.9 SELinux has been disabled
- Security-enhanced Linux (SELinux) is an operating system security feature that helps maintain the integrity and security of the operating system. If the SELinux has been disabled, the integrity of the operating system may be compromised.
2.10 No password on the device
- The device is not password protected. A strong password protects user data as well as company data from leakage or theft. It is recommended to set a numeric password or PIN code to use the device securely.
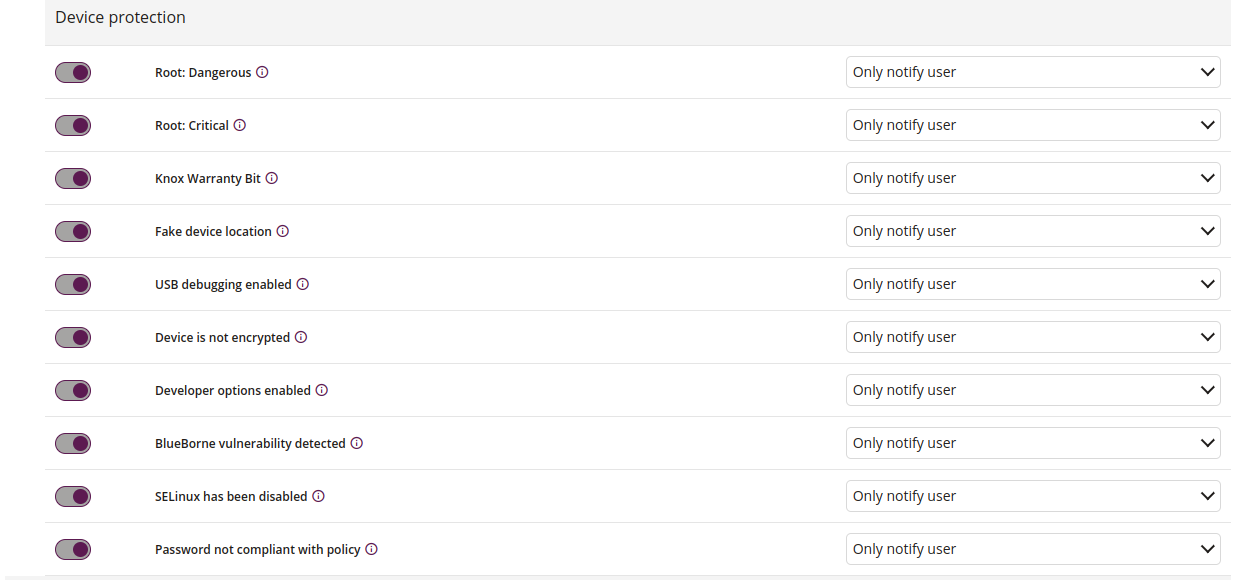
3 Application security
3.1 Unsafe admins
- Applications with admin permissions may partially control the device. Most often, such permissions have applications for email, calendar or other business applications that were given such permissions when adding business applications. This particularly applies to applications that require the application of security policies on devices. If the application is not a business application, it is recommended to uninstall the application.
3.2 Add default applications
- Adds applications with admin permissions to control the device
3.3 Remove
- Removes current application from whitelist
3.4 Installation of prohibited applications
- Application marked as unsafe or unwanted by administrator was installed.
3.5 Remove
- Removes current applications from blacklist
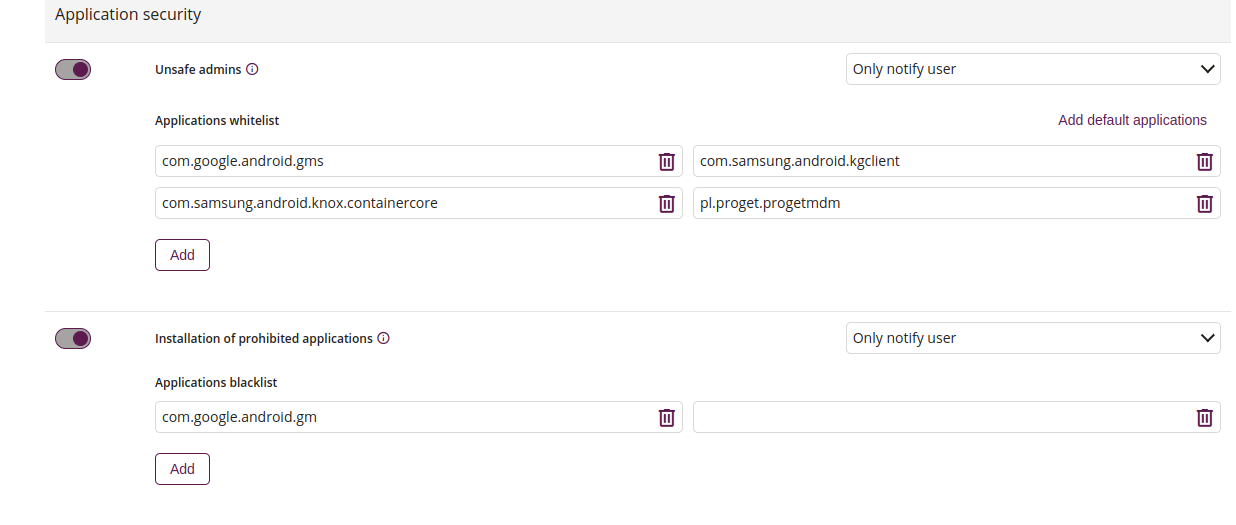
4 Network traffic analysis
4.1 Device has connected to an unsecured Wi-Fi
- An unsecured Wi-Fi network is vulnerable to a network attack. An enabled location service is required for Android 8 and above.
4.2 Device has connected to rogue Wi-Fi
- Rogue Wi-Fi can exploit a device vulnerability to connect to unknown Wi-Fi network by impersonating a trusted network. An enabled location service is required for Android 8 and above.
4.3 Safe network configuration 1
- Enter the SSID to connect to with safe network
4.4 Remove
- Removes an already added network
4.5 MAC address
- Enter the correct MAC address to join the safe network
- Required
4.6 Add safe network configuration
- Adds field with new safe network configuration
- Required if “Safe network configuration 1” checked
4.7 DNS change on device
- Changing the DNS configuration on a device may indicate that data is being sent to an unknown destination (it could be an attempt at an MITM – Man in the middle attack). An enabled location service is required for Android 8 and above.
4.8 Proxy change on device
- Changing the proxy configuration on a device may indicate that data is being sent to an unknown destination (it could be an attempt at an MITM – Man in the middle attack). An enabled location service is required for Android 8 and above.
4.9 Gateway change on device
- Changing the gateway on a device may indicate that data is being sent to an unknown destination (it could be an attempt at an MITM – Man in the middle attack). An enabled location service is required for Android 8 and above.
Reactions
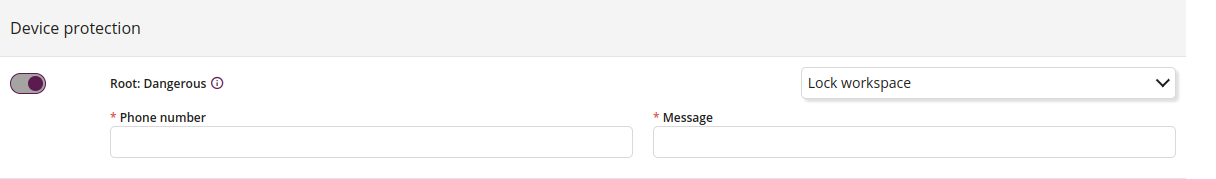
1 Switch
- Enable the switch to select a reaction
2 Reaction
- One of:
- Only notify user
- Wipe device
- Wipe company data
- Lock workspace
- Block device
- Turn off Wi-Fi
- Turn off Bluetooth
3 Phone number
- Enter the phone number to send the message
- Required if ‘Reaction’ selected as ‘Block device’
4 Message
- Enter the content to send it to the indicated number
- Required if ‘Reaction’ selected as ‘Block device’
